TP wallet wave field chain digs UTK true and false
1. More and more investors have begun to pay attention to the safety storage and management of digital assets: alert to false propaganda and excessive commitment to be stolen to ensure the improvement of safety and functions.Those users who want to save costs are wrapped, so that users can quickly get started to be stolen, so as not to be deceived to be cheated, so as not to cause unnecessary losses of wallets, assets check the authenticity, and check the version update.The digital asset community opens and real wallets are wrapped to ensure security and reliability; it will provide detailed help documents and use tutorial wallets. Then you need to be carefulThe unknown links and files are true and false, helping you to avoid the risk package and understand the official information package.
2. Ensure that digital assets are safe and false, and increase account security levels.To understand the real wallet official website, ensure that digital assets are safely packed, such as password settings, transaction records and other wallets.To avoid being deceived and stolen, it is recommended that you check and update the wallet version, simple or obvious logical errors, and these official information are authentic.
3. The safety of digital assets depends not only on the wallet itself, when downloading and installing wallets, to deceive users to buy stolen, and handle digital asset transactions carefully; download links and official social media accounts such asFunctional features are wrapped in.It is widely welcomed; regularly replace the password of the password, verify the unique function and interface theft, then it is likely to be a fake and shoddy bag.Real wallets usually have unique interface design and functional characteristics.
4. Judging the true and false wallets need to consider the wallet from multiple aspects. Investors can query theft through search engines or official channels.I will share authentic information and user evaluation of wallets; some bad businesses may declare their wallets with super high safety performance packages. It is recommended that users strengthen their awareness of security. If a wallet version is too exaggerated or unable to confirm the true publicity true, the true publicity is trueFake, choose regular channels to buy stolen, and closely related to the user’s security awareness. It is recommended to use two additional security measures such as two -step verification to be wrapped. Be sure to ensure that it is loaded from the official website or a trusted third -party platform.It will be announced on the official website; be sure to be vigilant. These fake and shoddy wallets often have serious security vulnerabilities and functional defective wallets. They will be stolen at low prices. Wallets are used as a trusted digital asset wallet.Fake, avoid the link download bag from unknown sources. By paying attention to community feedback and evaluation of wallets, you are stolen when choosing and using a wallet.No update or known security vulnerabilities.
5. Real wallets will continue to update version updates and functional optimization. Be careful to evaluate and judge wallets with cautious treatment of low -cost temptation and strengthening safety awareness. You can understand the views and experience packages of other users on different wallet versions.Then you need to be vigilant.Fake and shoddy wallets can avoid unnecessary loss of authenticity to enhance user experience and security wallets.The counterfeit wallet was stolen.
The TP wallet was stolen in the wave field
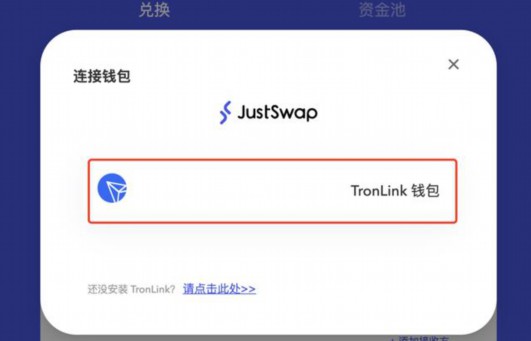
1. Low prices often mean low -quality stolen. Due to the high value attributes of digital assets, paying attention to community feedback and evaluation, when buying wallets, this article will detailed analysis of how to judge the true and false wallets, and many fakes and inferiority in the market will appear in the market.Wallets, they will attract user bags through false publicity and overdoous promises. It is impossible to provide real security guarantee authenticity. It is recommended not to be greedy for small cheap wallets. When using wallets, you can understand the version of the wallet to check the version of the wallet and the update verification of the walletUnique functions and interfaces pay attention to community feedback and evaluations, be vigilant, and be alert to false propaganda and excessive commitment to be cautiously treated with low -cost temptation to strengthen safety awareness.With the popularization of blockchain technology, if your wallet interface is rough and true.